7. May 2024 By Michael Mamerow
NIS 2 ante portas: How CISOs can sleep more soundly with Microsoft
You probably know the most clichéd underdog legend of mankind - David versus Goliath. NIS 2 can seem like an invincible giant in many ways to an organisation that has to be compliant by 18.10.2024 and was previously unregulated. The world of cyber threats naturally continues to turn in parallel with the urgent implementation of the directive, and even seems to be approaching us inexorably and, thanks to GenAI, unfortunately ever faster.
Ransomware as a Service (RaaS) and Hacking as a Service (HaaS) are also increasing the number of attacks and leading to rising incident response costs. True to the motto "after the audit is before the audit", the pressure on employees and teams around the Chief Information Security Officer (CISO) and in IT operations is increasing.
While the individual controls of NIS 2 may still seem somehow feasible at the planning stage, when you look at the timetable and the available heads, the seemingly insurmountable Goliath looms before you again. In our experience, it takes at least six months to fully implement the critical and important NIS 2 requirements - starting from scratch - just to set up or reorganise IT security accordingly. Prerequisite: The basic principles, such as Zero Trust, have already found their way into IT.
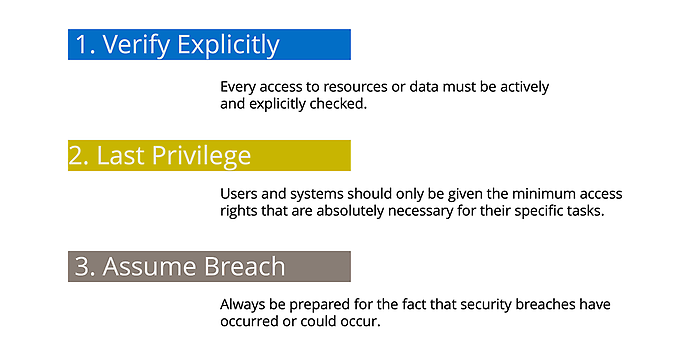
The Zero Trust Principles
Six months - an absolute minimum - so many CISOs and those responsible for them are currently neither sleeping soundly nor deeply.
In addition to necessary changes in the organisation and processes, such as new reporting obligations to the Federal Office for Information Security (BSI), the focus of NIS 2 is on IT security, which is already burdened by cloud transformation projects. Too few heads in IT for too many planned measures certainly also corresponds to your image of IT as a defeated David in a defensive battle.
However, as the Bible reports, David was very calm before his battle and spoke confidently to those around him. He had probably slept well, because his choice fell on a good, clever and familiar solution. A handy slingshot that - when it came down to it - took out the walking troublemaker with precision.
The right choice of tools, learnt, practised and used correctly in practice, often makes all the difference - especially in IT. As a goatherd, David had years to get "in shape" - your organisation does not have this time for NIS 2.
If the image of NIS 2 equalling Goliath seems to you to be consistent up to this point, then you are probably also one of those people who frown sceptically when Delivery, as David personified, assures you with conviction that - despite all indicators to the contrary - everything is under control and the requirements of NIS 2 will be met by October 2024. As CISO, you may even bear overall responsibility for demonstrable implementation so that, in the event of an incident, the executive bodies or the organisation are not threatened with fines or even personal liability. Quiz question: Does your IT perhaps have a hidden slingshot? Unfortunately, very often we don't find such a tool in our assessments at the moment.
You can guess where I'm going with this comparison. Microsoft has already built a customised slingshot for/against NIS 2. The following graphic shows the respective products that address the NIS 2 Principles today.

Products that address the NIS 2 Principles today, source: https://www.itgovernance.co.uk/nis-regulations-cyber-assessment-framework
Of course, you don't just have Microsoft in your organisation. The slingshot may be shaped differently in detail, have a longer rubber band or a longer handle - this is not decisive as long as certain principles such as Zero Trust apply and NIS 2 is also considered at organisational and process level. Nevertheless, it makes sense to utilise the entire IT security suite from Microsoft, as the wonderful phrase "it is more than the sum of its parts" applies here.
You might now ask whether this isn't more a question of faith and I would answer: "Yes, because faith in the functionality of his slingshot also worked well for David." Stop! Of course, when it comes to Microsoft technologies, I don't mean spiritual faith like David's, but rather a fact-based assessment that ultimately leads to the conviction that the interaction of various Microsoft security tools, not just in relation to NIS 2, will ensure that future threats and regulatory requirements are always met and defeated between the eyes.
We see time and again with our customers that either all or almost all licences are available for a comprehensive and extensive use of Microsoft's security products. The use of these tools would not involve higher running costs and could initially only take place in read-only reporting mode in order to collect data and gain a more accurate view of IT security. At the same time, licences can be saved by sharing the covered tools. IT security is thus homogenised step by step.
The comprehensive measurement of the maturity level of IT security using the Microsoft Security Score or the evaluation of NIS 2 controls using the Microsoft Purview Compliance Manager alone provide IT operations and the CISO with valuable real-time information for compliance.
Microsoft Security Tools for NIS 2 - the ideal slingshot
So what should the perfect tool for NIS 2 look like? It is certain that the German legislation will have its deviations from the EU legislation. It can be deduced from the draft bills that, in the end, compliance will lie between KRITIS and EU NIS 2. We therefore do not yet know exactly what the perfect slingshot must look like, but as the slingshots for KRITIS and EU-NIS 2 are known, we should not wait for the law to be passed.
On the contrary, given the extremely short implementation deadline of October 2024, it is imperative that initial measures are implemented.
The following topics are addressed and tightened up by NIS 2:

Topics influenced by NIS 2
Microsoft has already integrated corresponding controls into all relevant products so that an analysis and proactive assessment of its own IT security can be carried out relatively quickly. Parallel to the publication of the law, Microsoft will tighten up and quickly close the gap to the current state of knowledge. The advantage for you: The gap in your own organisation can already be minimised today.
The configuration makes a huge difference - sharp stones are a must
However, one secret ingredient of David is not mentioned in the Bible: his stones. The type of ammunition can also greatly influence the result, especially the throwing efficiency in terms of speed, direction and effect. Imagine if David had used a flat stone instead of a pointed one. The stone would have either flown past Goliath or bounced off with a roar of laughter. So let's agree that the slingshot alone would not have defeated Goliath.
For me, this is comparable to the configuration of security tools. From antivirus scanners to security information and event management (SIEM), the right configuration, abstractly speaking the data processing of the respective tool, no longer only influences the efficiency and effectiveness of a tool. It is a fallacy to believe that the perfect configuration has been found in the tools used today. Continuous testing and improvement is a must. Otherwise you are throwing flat stones. Newly introduced functions are often overlooked in day-to-day operations because there is simply not enough time to evaluate them. It's better not to even talk about the interaction between the tools.
However, the weakest link in the long chain of security tools will break in the event of a serious cyberattack and render the rest worthless. Ongoing assessments, but also the reporting and recommendations of the manufacturers themselves, are therefore a valuable starting point for achieving a healthy level of maturity - also in the context of NIS 2.
Microsoft's range of products and services are integrated across all levels - from the IoT agent on the handheld scanner to the automatic analysis and processing of anomalies in Microsoft Sentinel and Copilot for Security. This provides invaluable added value for all administrators, analysts and decision-makers, giving them a common overview and perspective.
Everything has to work in the event of an attack - the momentum
There was just one crucial component missing in this seemingly unequal epic battle: perfect execution. David had to execute a perfect throw from a standing position. He didn't get a second chance, because Goliath would certainly have taken countermeasures immediately after the first miss. The situation is similar with your organisation, regardless of whether you are referring to NIS 2 or thinking of possible cyber attacks in general. A serious attack must be repelled with the first roll.
However, the perfect throw requires the perfect interplay of tool (slingshot) and configuration (stones). Throw training, arm movement, body balance, foot position, hand-eye coordination and many other factors all come together in one moment. External parameters, such as the perception of weather and wind conditions, also play a small but important role.
The smooth data processing chain, the correct analysis of all signals and the right reaction to them, i.e. the decisive throw, is only possible if everything works together as a matter of course. The functioning automatism that we want to achieve in cyber defence through Security Orchestration (SOAR) and Extended Detection and Response (XDR) can only be successful under these conditions.
Faith helps security - strong partners help with security
Your IT department is certainly a bit like David. Now, not everyone has been a goatherd for years and knows the slingshot or its equivalent inside out. Daily training with security tools on a greenfield site, thin staffing levels, no budget to protect yourself with thick armour.
Does this sound familiar?
Now add AI-based cyberattacks and new regulations such as NIS 2 and you not only feel like David, but are basically in the same situation. Everyday life collides with new challenges. Goliath is getting closer and closer. This is where we, as Trusted Advisors for IT security, like to come into play.
Assuming David had not had divine assistance and years of experience - what would have been a possible solution? The most obvious solution would certainly have been to seek advice and help in his immediate environment and to prepare himself as best as possible (training). For example, finding an experienced goatherd who has won competitions in stone throwing. This would not have been possible for David because, according to legend, he was not at home with his sheep but in the army of the Israelites. Often, none of the direct colleagues have the necessary knowledge to realise time-critical requirements (for example, before the next audit) on time.
What could David do in this case? Not much. With a bit of luck, one of the army veterans standing nearby could have taught him a few tricks with a sword, but the outcome of the unequal battle would certainly have been different.
Fortunately, the world has moved on and adesso, as a long-standing partner, is very familiar with Microsoft's slingshot. With appropriately certified specialists, the necessary stones are polished on a daily basis and with over 12,000 adessis, we can also serve the upcoming Goliath NIS 2 with the necessary momentum on schedule.
Finally, let's come back to the biggest hurdles in connection with NIS 2 and thus to the unvarnished reality. The decision to use Microsoft Security Tools would probably be quickly affirmed by everyone if a greenfield approach were possible, but I have not yet met such a customer. Your organisation is probably also represented by a colourful bouquet of different manufacturers - certainly including some Microsoft products - so we are talking about a very high degree of heterogeneity and complexity here. A wide variety of licences are in circulation, information about anomalies can be found in various tools or portals, the next audit is in sight and the next holiday or partial sick leave won't let you sleep any easier.
We know the situation, understand the complexity and recommend a tried-and-tested solution, specifically for NIS 2 - let's symbolically construct your slingshot for NIS 2 together and get talking so that you can sleep soundly again soon.
Would you like to find out more about exciting topics from the world of adesso? Then take a look at our previous blog posts.
Also interesting:

